Home > News & Blog > Are You Ready for ETSI EN 303 645?
Are You Ready for ETSI EN 303 645?
Cyber Security for Consumer Internet of Things: Baseline Requirements

With data breaches, device hacks and systems with poor security being regularly exploited, the push for a complete security overhaul in our devices is being driven more than ever.[1] In this series of blog posts, we will discuss what the future holds for our devices; the interconnectivity between them; and how security needs to begin from the bare metal of the microchips that are designed, programmed, and implemented in our ‘smart’ technology.[2]
What is ETSI EN 303 645?
“As more devices in the home connect to the Internet, the cyber security of the Internet of Things (IoT) becomes a growing concern. People entrust their personal data to an increasing number of online devices and services. Products and appliances that have traditionally been offline are now connected and need to be designed to withstand cyber threats.”
ETSI EN 303 645 brings together widely considered good practice in security for Internet-connected consumer devices in a set of high-level outcome-focused provisions.
Outlined in both the standard, and this article, are the provisions that are considered for outcome-focused security solutions, appropriate for the relevant products. ETSI EN 303 645 provides a set of baseline provisions applicable to all consumer IoT devices. [3]
The standard outlines 13 key provisions which need to be observed and met for all new devices.
These are:
- No universal default passwords
- Implement a means to manage reports of vulnerabilities
- Keep software updated
- Securely store sensitive security parameters
- Communicate securely
- Minimize exposed attack surfaces
- Ensure software integrity
- Ensure that personal data is secure
- Make systems resilient to outages
- Examine system telemetry data
- Make it easy for users to delete user data
- Make installation and maintenance of devices easy
- Validate input data
Each of these provisions have sub provisions which identify and explain best practices and actions to keep consumers protected and secure.
In this first section, we will cover provisions 1 to 3.
Provision 1: No universal default passwords
 For any IoT devices provided to consumers, where passwords are used, these passwords will need to be unique for every device. These passwords will either be per device or defined by the user. Prior to a user being able to add their own password to a device, the pre-installed password that ships will be generated by mechanisms that reduce the risk of automated attacks successfully infiltrating the device. With any devices that are released to consumers, it is important to ensure that the authentication methods and mechanisms that are used are appropriate and incorporate the best practices from cryptography. The appropriate mechanisms are determined by the properties of the technology, the risks that could incur from malicious hacking, and the usage of the device.
For any IoT devices provided to consumers, where passwords are used, these passwords will need to be unique for every device. These passwords will either be per device or defined by the user. Prior to a user being able to add their own password to a device, the pre-installed password that ships will be generated by mechanisms that reduce the risk of automated attacks successfully infiltrating the device. With any devices that are released to consumers, it is important to ensure that the authentication methods and mechanisms that are used are appropriate and incorporate the best practices from cryptography. The appropriate mechanisms are determined by the properties of the technology, the risks that could incur from malicious hacking, and the usage of the device.
For devices that allow user authentication, the devices need to provide the user with a mechanism to change the authentication value that is used. This mechanism needs to be simple for any user or administrator to use, to ensure that a user is capable of changing the authentication value with minimal expertise.
When the IoT device is not a constrained device (a typically low power device that can handle a specific application purpose which communicate wirelessly [4]), mechanisms need to be available to effectively make network based brute force attacks impracticable. In essence, a device should be capable of blocking against any network attacks on authentication.
Provision 2: Implement a means to manage reports of vulnerabilities
 Device manufacturers will now need to make vulnerability disclosure policies publicly available. These policies must include a minimum framework to ensure safety and security for customers. These minimum requirements are for contact information to be available for reporting issues, as well as providing information on timelines for receipt acknowledgements, and status updates until the issue is resolved.
Device manufacturers will now need to make vulnerability disclosure policies publicly available. These policies must include a minimum framework to ensure safety and security for customers. These minimum requirements are for contact information to be available for reporting issues, as well as providing information on timelines for receipt acknowledgements, and status updates until the issue is resolved.
Any vulnerabilities that are disclosed need to be worked on in a timely manner to ensure customer safety, and device manufacturers will need to continually monitor for, and identify security vulnerabilities. These vulnerabilities will need to be rectified within the products and services provided by the manufacturers and must be supported for the period defined.
Provision 3: Keep software updated
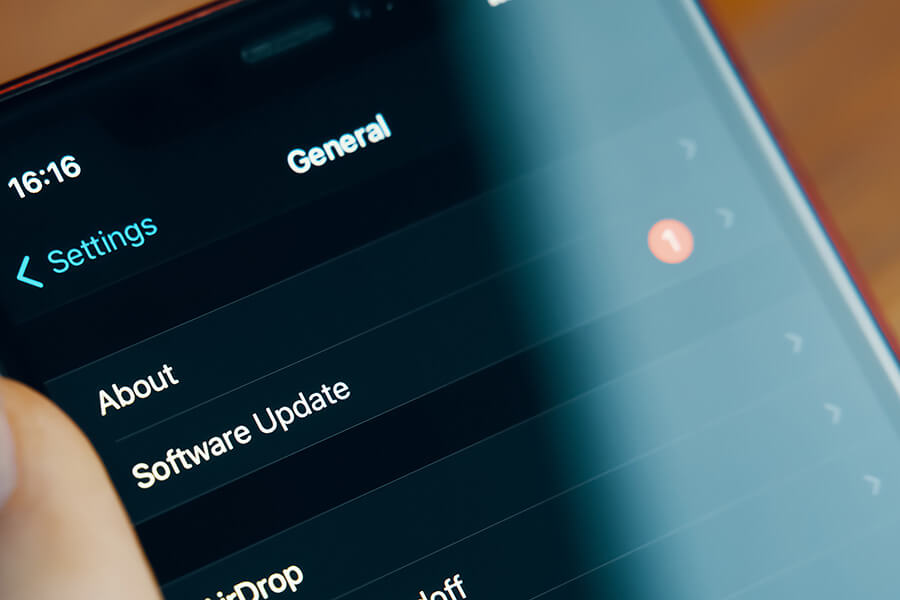 For IoT devices, it is important to keep the software regularly updated. This isn’t just for performance enhancements of the device, but also for closing any vulnerabilities and ensuring the safety and security of the devices for the end user. Updates over the air (via an internet connection) should be timely and verified for authenticity and integrity via a trust relationship. The updates provided need to be come from a secure mechanism using the best practices in cryptography, as side-loading updates creates a very easy route for malware to be injected. An update shall be simple for the user to apply, and automatic mechanisms should be used for software updates, as end users would not practicably know when to update or how to update the device if the method is not straightforward. The update checks are to be performed after the device is configured/switched on, and then periodically.
For IoT devices, it is important to keep the software regularly updated. This isn’t just for performance enhancements of the device, but also for closing any vulnerabilities and ensuring the safety and security of the devices for the end user. Updates over the air (via an internet connection) should be timely and verified for authenticity and integrity via a trust relationship. The updates provided need to be come from a secure mechanism using the best practices in cryptography, as side-loading updates creates a very easy route for malware to be injected. An update shall be simple for the user to apply, and automatic mechanisms should be used for software updates, as end users would not practicably know when to update or how to update the device if the method is not straightforward. The update checks are to be performed after the device is configured/switched on, and then periodically.
Some devices may have the option of automatic updates and notifications for such updates. During the first-time setup (initialisation) these should be enabled by default but configurable by the user in case they wish to disable or postpone security updates and/or notifications about these updates. Alongside notifications about updates, any information as to the purpose of the update, including risks that will be mitigated, should be provided and easily accessible.
As is common when updating software-based devices, users are often unable to use the device either partially or completely – think about when you’re using a PC and it forces an update which can take an age. For IoT devices, any updates need to notify the user if functionality will be affected during the update process.
For all devices that require regular updates for safety and security, manufacturers will need to clearly publish the support period in a way that is clear to end users and is easy to find. This is because devices eventually move into the discontinued stage and newer more complete devices become available. To avoid customers experiencing issues with device management and support, ensuring they are aware of the support period mitigates any problems.
For some constrained IoT devices, updates are not always possible. In these circumstances, it needs to be made clear by the manufacture why the lack of software updates exists. In these circumstances, it may be necessary for the physical hardware of the device to be replaced and if this is the case, it needs to be made clear in the support documentation by the manufacturer.
In part 2, we will discuss/review the provisions for secure storage mechanisms; the measures required for secure communication between your IoT device and the internet; and how to minimize the probability of your IoT device being exposed to the internet.
EPS Global provides simple, cost-effective Secure Provisioning services from our state-of-the-art programming centers strategically located in all major electronic manufacturing hubs worldwide. Talk to us today about end-to-end security solutions for your next project.









